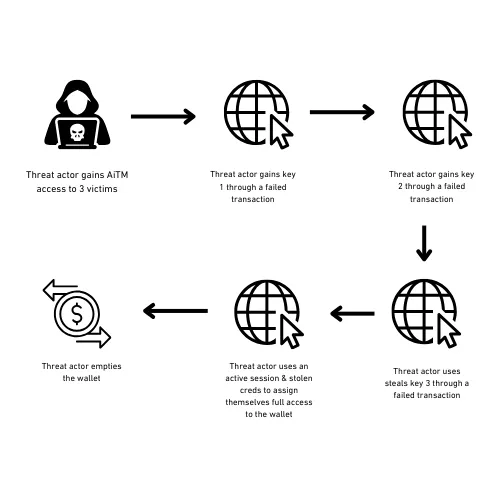
🛡️ 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗡𝗲𝘄𝘀 & 𝗜𝗻𝘁𝗲𝗹𝗹𝗶𝗴𝗲𝗻𝗰𝗲 𝗦𝘂𝗺𝗺𝗮𝗿𝘆
🔍 𝗧𝗵𝗿𝗲𝗮𝘁 𝗟𝗮𝗻𝗱𝘀𝗰𝗮𝗽𝗲 𝗢𝘃𝗲𝗿𝘃𝗶𝗲𝘄
𝗢𝘃𝗲𝗿𝗮𝗹𝗹 𝗦𝗲𝘃𝗲𝗿𝗶𝘁𝘆: 🟠 MEDIUM
𝗞𝗲𝘆 𝗧𝗿𝗲𝗻𝗱𝘀:
• Interesting use of Microsoft Outlook features for C2 (FinalDraft)
• Exploitation of legitimate services for malicious purposes
𝗠𝗼𝘀𝘁 𝗧𝗮𝗿𝗴𝗲𝘁𝗲𝗱 𝗦𝗲𝗰𝘁𝗼𝗿𝘀: Government, Telecommunications, Healthcare
Key Takeaways
🟠 𝗠𝗶𝘁𝗶𝗴𝗮𝘁𝗲 𝗥𝗶𝘀𝗸𝘀 𝗳𝗿𝗼𝗺 𝗙𝗶𝗻𝗮𝗹𝗗𝗿𝗮𝗳𝘁 𝗠𝗮𝗹𝘄𝗮𝗿𝗲
𝗗𝗲𝘀𝗰𝗿𝗶𝗽𝘁𝗶𝗼𝗻:
Investigate for Microsoft Outlook configurations to detect exploitation via the FinalDraft malware, which uses email drafts for command-and-control communications. We’d reccomend using the information provided by ElasticLabs in their fantastic report.
𝗥𝗮𝘁𝗶𝗼𝗻𝗮𝗹𝗲:
This stealthy malware can exfiltrate sensitive data and perform lateral movement within networks, posing significant risks to organisations.
𝗧𝗶𝗺𝗲𝗳𝗿𝗮𝗺𝗲: 𝗔𝗰𝘁𝗶𝗼𝗻 𝗥𝗲𝗾𝘂𝗶𝗿𝗲𝗱 𝗧𝗵𝗶𝘀 𝗪𝗲𝗲𝗸
𝗦𝗼𝘂𝗿𝗰𝗲𝘀:
- https://www.elastic.co/security-labs/finaldraft
- https://www.bleepingcomputer.com/news/security/new-finaldraft-malware-abuses-outlook-mail-service-for-stealthy-comms/
🔴 𝗣𝗮𝘁𝗰𝗵 𝗩𝘂𝗹𝗻𝗲𝗿𝗮𝗯𝗶𝗹𝗶𝘁𝗶𝗲𝘀 𝗶𝗻 𝗣𝗔𝗡-𝗢𝗦 𝗮𝗻𝗱 𝗖𝗶𝘀𝗰𝗼 𝗗𝗲𝘃𝗶𝗰𝗲𝘀
𝗗𝗲𝘀𝗰𝗿𝗶𝗽𝘁𝗶𝗼𝗻:
This was also in yesterday’s new but we strongly recommend that you immediately update affected systems to address the high-severity authentication bypass vulnerabilities in PAN-OS and the exploitation of unpatched Cisco devices.
𝗥𝗮𝘁𝗶𝗼𝗻𝗮𝗹𝗲:
Exploitation of these vulnerabilities has been observed in the wild, posing critical risks to network security.
𝗧𝗶𝗺𝗲𝗳𝗿𝗮𝗺𝗲: 𝗜𝗺𝗺𝗲𝗱𝗶𝗮𝘁𝗲 𝗔𝗰𝘁𝗶𝗼𝗻 𝗥𝗲𝗾𝘂𝗶𝗿𝗲𝗱
𝗦𝗼𝘂𝗿𝗰𝗲𝘀:
• https://cybersecuritynews.com/pan-os-authentication-bypass-exploited/
• https://cybersecuritynews.com/salt-typhoon-hackers-exploited-1000-cisco-devices/
🔵𝗜𝗺𝗽𝗹𝗲𝗺𝗲𝗻𝘁 𝗘𝗻𝗵𝗮𝗻𝗰𝗲𝗱 𝗣𝗿𝗼𝘁𝗲𝗰𝘁𝗶𝗼𝗻 𝗶𝗻 𝗚𝗼𝗼𝗴𝗹𝗲 𝗖𝗵𝗿𝗼𝗺𝗲
𝗗𝗲𝘀𝗰𝗿𝗶𝗽𝘁𝗶𝗼𝗻:
Enable the AI-powered Enhanced Protection feature in Google Chrome to provide real-time threat detection, suspicious download scanning, and password compromise alerts.
𝗥𝗮𝘁𝗶𝗼𝗻𝗮𝗹𝗲:
This feature significantly enhances user security by proactively identifying and mitigating threats that may not have been previously recognised.
𝗧𝗶𝗺𝗲𝗳𝗿𝗮𝗺𝗲: In the next month
𝗦𝗼𝘂𝗿𝗰𝗲𝘀:
• https://www.bleepingcomputer.com/news/google/google-chromes-ai-powered-security-feature-rolls-out-to-everyone/
• https://cybersecuritynews.com/google-chrome-ai-powered-security/