TLDR: Highly capable adversaries are now performing incredibly difficult to detect AiTM attacks that target multi-signer systems, and these TTPs are a critical threat against banking systems, or systems that hold key material for signing anything from drivers to transactions.
Introduction
There’s been a lot of news about the quantity of billions of crypto from BytBit in late February 2025 but appears this campaign started with WazirX in July 2024, continued with Radiant Capital in October 2024, and ByBit is just the latest (and largest victim). And at first glance you’d think ok the crypto exchange was compromised, not much to see here. But AuditUrContracts did a fantastic job analysing the WazirX intrusion and demonstrated these where attacks conducted by persistent and capable adversaries. It wasn’t a simple web bug, or a single phishing email, but the compromise of multiple, very specific individuals. There is critical lessons to be learn from these intrusions by both the web3 community and the cyber security community at large.
Background
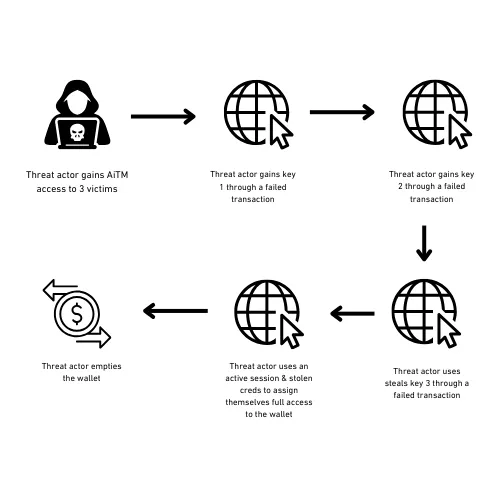
On July 18th, 2024 Cyvers Alerts on X/Twitter identified $235 million worth of suspicious transactions ETH transactions from WazirX that then went to various tumblers. Based on statements from WazirX, Liminal and AuditUrContracts’s analysis somehow what the user saw, and input into the Liminal website to authorise transactions was changed in transit. The threat actor also used their access to this data to undertake a series of steps to gather the required signatures and data to execute the attack. There’s a lot more detail in this write up from AuditUrContracts and Liminal but basically the threat actor used their Adversary in The Middle (AITM) access to steal key material by changing the contents of the website the 3 signers where using. They then used a compromised active session and the 3 stolen signing keys to initiate a transaction that resulted in them having full access to the wallet and they then drained it.

And it’s important to note, that all failed transactions would’ve been noticeable to the victims.
Lesson for the non Web3 World
So at first glance this seems like a highly specific threat against web3 (crypto) targets, however, it demonstrates the persistence, capability and intent of these threat actors to target multi-signing systems and perform difficult to detect Adversary in The Middle attacks. So for any organisation that deals with transferring large sums of money (think pay runs, mergers, paying large invoices, banks) there’s a risk. But also, any multi signing process, for example signing code, certificates etc. Whilst web3 is being targeted due to the ease of transferring funds, we have seen North Korean adversaries target traditional financial systems before, think back to the Bangladesh Central Bank heist. So if a target arises, I have no doubts they will once again pivot. Also, other threat groups will be interested in stealing key material that is normally done through a multi-signer process before, and we’ve seen key material being stolen with the Microsoft 2023 breach. As a result, it’s crucial that organisations don’t assume that just because multiple people need to approve something it’s safe or low chance of being compromised.
So some of the key take aways are:
- For highly sensitive or high value transactions, have a dedicated machine or system that’s disconnected from everything else and can only talk to the system in question. The least friction way would be to have some dedicated virtual machines that are highly locked down and not part of your normal Active Directory/MDM/management tenant, and don’t save state. (ideally this would be physically seperate hardware but in a lot of cases that’s unworkable).
- Ensure there is monitoring and alerting on failed transactions, especially from highly privileged users. If there’s a failure ensure there’s a pause and in-depth investigation as to why…
- Friction is good for transactions, friction makes people stop and think. I believe security in general should be frictionless, but for certain things friction is critical
- Understand your threat groups. If you have signing material for drivers, large financial transactions or access to critical system that can’t fail you will be a target. It’s critical to understand how they do it, and what steps you can take to combat it.
- Harden your systems, reduce their attack surface, on mac or iOS devices us lockdown mode for anything that touches sensitive systems.
Lesson for the Web3 World
Take the lessons from the web2 world, sometimes you need to move slow to be fast. Whilst the Web3 world has a lot of it’s own nuances and the underlying workings of the technology differ from web2 the cyber security challenges we are seeing today are the same, except at a much much larger scale due to the sheer volume of money involved and the small size of the organisations. So pick a security partner who understands cyber security & start-up world and can help you. You will be targeted by insiders, North Korea and a laundry list of other threat groups. They want your money and we have seen a huge amount of organisations go under due to security challenges.